About This Course
NIST CSF 2.0 UPDATES
NCSE Course in 1 Minute
“Teaches You How to Establish, Assess and Operationalize a Cyber Security Program Based on the NIST Cyber Security Framework”
The NCSE (NIST Cyber Security Expert) certification course has been developed to teach businesses how to establish and operationalize a cyber security program based on the NIST Cyber Security Framework. This non-tech syllabus aimed at business leaders and/or cyber security practitioners has been developed based on a holistic body of knowledge that encompasses a real-life pragmatic approach to understanding the fundamental concepts of cyber risk management and how to leverage the NIST Cyber Security Framework in order to assess, implement and operationalize a cyber security program. No previous cyber security knowledge is assumed and the course is appropriate for all levels.
Our Partners
More Info
NIST CSF 2.0 UPDATES
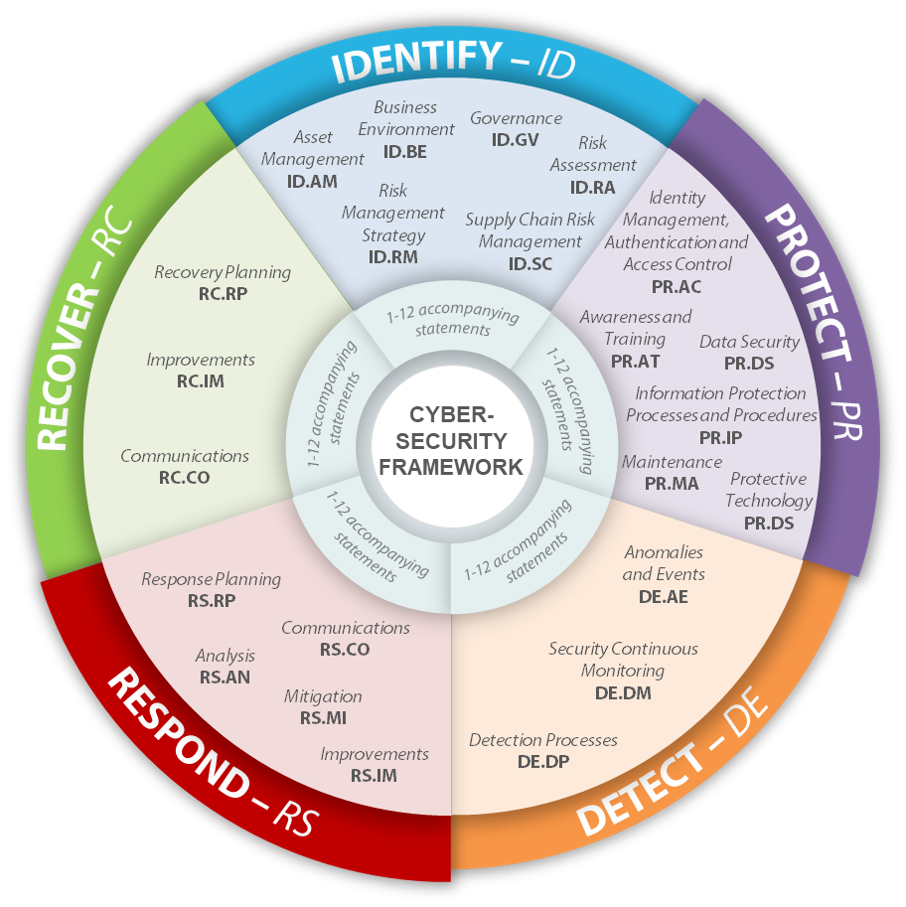
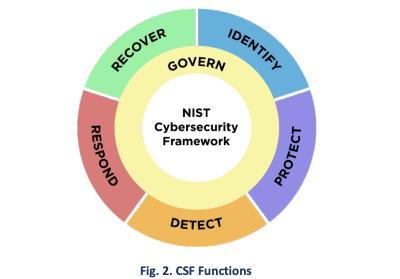
On February 26, 2024, the National Institute of Standards and Technology (NIST) introduced the updated version 2.0 of the Cybersecurity Framework (CSF). This new version builds upon the previous version 1.1, which has been in use since its release on April 16, 2018, succeeding the original framework established on February 12, 2014.
The latest version 2.0 brings significant advancements, particularly in the management of organizational governance and the security of supply chains. Starting April 15, 2024, we are providing a new additional module aimed at those interested in comprehending the recent changes and ensuring a smooth transition from the earlier version 1.1 to the enhanced version 2.0.
What does the Course Cover?
The course is non-technical in approach and supports students on a 10 modules journey. You are provided with 24/7 access to all materials and are also supported with access to live learning support sessions. Successful certification is via continual assessments with weekly online exams.
Explore the Modules
The Course is for?
The course syllabus has been specifically designed to be collaborative and bring together business leaders of various disciplines within an organization. They are the key stakeholders in designing, implementing or supporting the cyber risk management program of an organization. Key cyber risk management stakeholders include:
- C-Suite
- CISO/CSO/CIO or CRO
- Head of IT/Security
- CCO Chief Compliance Officer
- Cyber Security/Risk/Compliance Teams
- Legal
- Procurement
- Head of Business Units
- Technology Leaders / Project Managers
- Management Professionals / Team Leaders
- Digital Consultants
How do you Learn?
The course is delivered entirely online. Students are provided with 90 days access to all the training material and exams.
Training material comprises of rich interactive media such as videos, infographics and course notes. There are many opportunities for collaborative learning via the discussion forums and you can leverage the portal to connect to other students around the world. All students also have access to scheduled remote live learning sessions, with an opportunity to directly liaise with the tutor.
There are 10 modules with an online exam at the end of each module. The pass score for each module is 80% and you must obtain an average score of 80% or higher across all modules to be successfully certified. You can re-sit each of the module exams three times if required during your 10 weeks.
Training material comprises of rich interactive media such as videos, infographics and course notes. There are many opportunities for collaborative learning via the discussion forums and you can leverage the portal to connect to other students around the world. All students also have access to scheduled remote live learning sessions, with an opportunity to directly liaise with the tutor.
There are 10 modules with an online exam at the end of each module. The pass score for each module is 80% and you must obtain an average score of 80% or higher across all modules to be successfully certified. You can re-sit each of the module exams three times if required during your 10 weeks.
What Support do I Get?
About the Head Tutor
FAQ
How do I get Certified?
Successful certification depends on several factors. The online course includes continual evaluation of your performance and competency.

Will it Help my Career?
There is a Global IT security skills shortages and it has now surpassed four million according to a recent industry survey.
Do I need to have a Cyber Security Background?
No. The syllabus has been developed for a non-technical audience. When technical concepts are referenced in any way, they are fully explained.
How do I Re-certify?
Certification lasts for three years from the date awarded. Form June 2023 a recertification exam will be available online at www.icttf.org
There will be a fee of €500 for the recertification exam or any resits required.
What does this course equip students with?
What is the Course Format?
The NCSE (NIST Cyber Security Expert) course is delivered entirely online with recorded videos, downloadable case books and interactive material.
What is the Pass Mark and How Does the Scoring Work?
The pass mark for successful certification on the NCSE course is 80% Students are continually evaluated during the course. The scoring criteria is as follows: Each Module Assessment Carries: 10%
What is the Cancellation Policy?
Where are the Terms and Conditions?
Where will my Certified Qualification be Recognized?
Our cyber risk certifications are recognized globally. This course has been accredited and benefits from dual certification by the International Compliance Association (ICA) and other respected bodies.