IRELAND: PUBLIC SECTOR CYBER SECURITY BASELINE STANDARD - FAQ's
SPONSORED BY CYBER RISK INTERNATIONAL
What is the PSCSBS?
The Public Service Cyber Security Baseline Standards are designed to create an acceptable security standard that can be revised over time to address new threats and vulnerabilities and to keep pace with new technologies and suppliers. The standards are based on the National Institute of Standards and Technology (NIST) Cyber Security Framework, which is a comprehensive framework for businesses and organisations to identify, assess, and address cyber security risks. The baseline standards are structured around five themes: identify, protect, detect, respond, and recover.
The identify theme focuses on understanding the structures, policies, and processes needed to manage cyber security risks to systems, assets, data, and capabilities. The protect theme focuses on developing and implementing appropriate and proportionate cyber security measures to protect essential services and systems. The detect theme focuses on developing and implementing the capabilities needed to identify, detect, and defend against a cyber security event that may have the potential to affect essential services and systems. The respond theme focuses on developing and implementing activities, prioritised through the organisation's risk management process, to take action to contain and minimise the impacts of a cyber security event. The recover theme focuses on developing and implementing the capabilities, prioritised through the organisation's risk management process, to restore essential services that were affected by a cyber security event.
Why and Where Did it Come From?
The cyber security baseline standard was created as part of the National Cyber Security Strategy 2019-2024, which outlines measures to improve the resilience and security of public sector ICT systems. The standard was formulated by the National Cyber Security Centre (NCSC) in conjunction with the OGCIO, and will be implemented across all public service bodies (PSBs). It is intended to foster a culture of cyber security and best practice across the public sector, and to address the multiple challenges related to ICT in the public sector. The standard will be aligned with international standards and will cover measures and controls related to staff training, identity and access management. The NCSC will provide support and guidance for compliance with the standard at the local level for PSBs. A government IT security forum will also be created to facilitate information sharing on best practice for cyber security and to support the deployment of the baseline security standard.
What are the Terms of Reference?
The National Cyber Security Strategy Baseline Measures outline the mandatory protective security outcomes that all public service bodies (PSBs) must achieve to improve the resilience and security of public sector information and communications technology (ICT) systems and better protect data and services. The government IT security forum will be a key factor in the deployment of the cyber security baseline standards for public service ICT. The baseline standards will include measures and controls related to staff training and identity and access management. Staff in the public service system must receive training on the basic elements of cyber security. This approach will help to maximise existing resources and provide an opportunity for staff to develop cyber security skills. The use of the terms "must," "will," and "shall" in the document indicates that the details are mandatory, while "may," "should," and "could" indicate that the details are discretionary.
Who does it apply to? - What is the Scope of the Standard?
The Public Service Cyber Security Baseline Standards Steering Group has presented a set of measures to create an acceptable security standard that can be revised over time to address new threats and vulnerabilities, and to keep pace with new technologies and suppliers. The cyber security baseline standards will apply to all public service bodies. The goal of the standards is to improve the resilience and security of public sector information and communications technology (ICT) systems and to foster a culture of cyber security and best practice across the public sector. The standards will be aligned with international standards and will cover measures and controls related to staff training, identity and access management. The National Cyber Security Centre (NCSC) will provide support and guidance for compliance with the standard at the local level for public service bodies. A government IT security forum will also be created to facilitate information sharing on best practice for cyber security and to support the deployment of the baseline security standard.
What Does it Look Like?
The Public Service Cyber Security Baseline Standards are designed to create an acceptable security standard that can be revised over time to address new threats and vulnerabilities and to keep pace with new technologies and suppliers. The standards are based on the National Institute of Standards and Technology (NIST) Cyber Security Framework, which is a comprehensive framework for businesses and organisations to identify, assess, and address cyber security risks. The baseline standards are structured around five themes: identify, protect, detect, respond, and recover.
The identify theme focuses on understanding the structures, policies, and processes needed to manage cyber security risks to systems, assets, data, and capabilities. The protect theme focuses on developing and implementing appropriate and proportionate cyber security measures to protect essential services and systems. The detect theme focuses on developing and implementing the capabilities needed to identify, detect, and defend against a cyber security event that may have the potential to affect essential services and systems. The respond theme focuses on developing and implementing activities, prioritised through the organisation's risk management process, to take action to contain and minimise the impacts of a cyber security event. The recover theme focuses on developing and implementing the capabilities, prioritised through the organisation's risk management process, to restore essential services that were affected by a cyber security event.
Why and Where Did it Come From?
The cyber security baseline standard was created as part of the National Cyber Security Strategy 2019-2024, which outlines measures to improve the resilience and security of public sector ICT systems. The standard was formulated by the National Cyber Security Centre (NCSC) in conjunction with the OGCIO, and will be implemented across all public service bodies (PSBs). It is intended to foster a culture of cyber security and best practice across the public sector, and to address the multiple challenges related to ICT in the public sector. The standard will be aligned with international standards and will cover measures and controls related to staff training, identity and access management. The NCSC will provide support and guidance for compliance with the standard at the local level for PSBs. A government IT security forum will also be created to facilitate information sharing on best practice for cyber security and to support the deployment of the baseline security standard.
What are the Terms of Reference?
The National Cyber Security Strategy Baseline Measures outline the mandatory protective security outcomes that all public service bodies (PSBs) must achieve to improve the resilience and security of public sector information and communications technology (ICT) systems and better protect data and services. The government IT security forum will be a key factor in the deployment of the cyber security baseline standards for public service ICT. The baseline standards will include measures and controls related to staff training and identity and access management. Staff in the public service system must receive training on the basic elements of cyber security. This approach will help to maximise existing resources and provide an opportunity for staff to develop cyber security skills. The use of the terms "must," "will," and "shall" in the document indicates that the details are mandatory, while "may," "should," and "could" indicate that the details are discretionary.
Who does it apply to? - What is the Scope of the Standard?
The Public Service Cyber Security Baseline Standards Steering Group has presented a set of measures to create an acceptable security standard that can be revised over time to address new threats and vulnerabilities, and to keep pace with new technologies and suppliers. The cyber security baseline standards will apply to all public service bodies. The goal of the standards is to improve the resilience and security of public sector information and communications technology (ICT) systems and to foster a culture of cyber security and best practice across the public sector. The standards will be aligned with international standards and will cover measures and controls related to staff training, identity and access management. The National Cyber Security Centre (NCSC) will provide support and guidance for compliance with the standard at the local level for public service bodies. A government IT security forum will also be created to facilitate information sharing on best practice for cyber security and to support the deployment of the baseline security standard.
What Does it Look Like?
Empty space, drag to resize
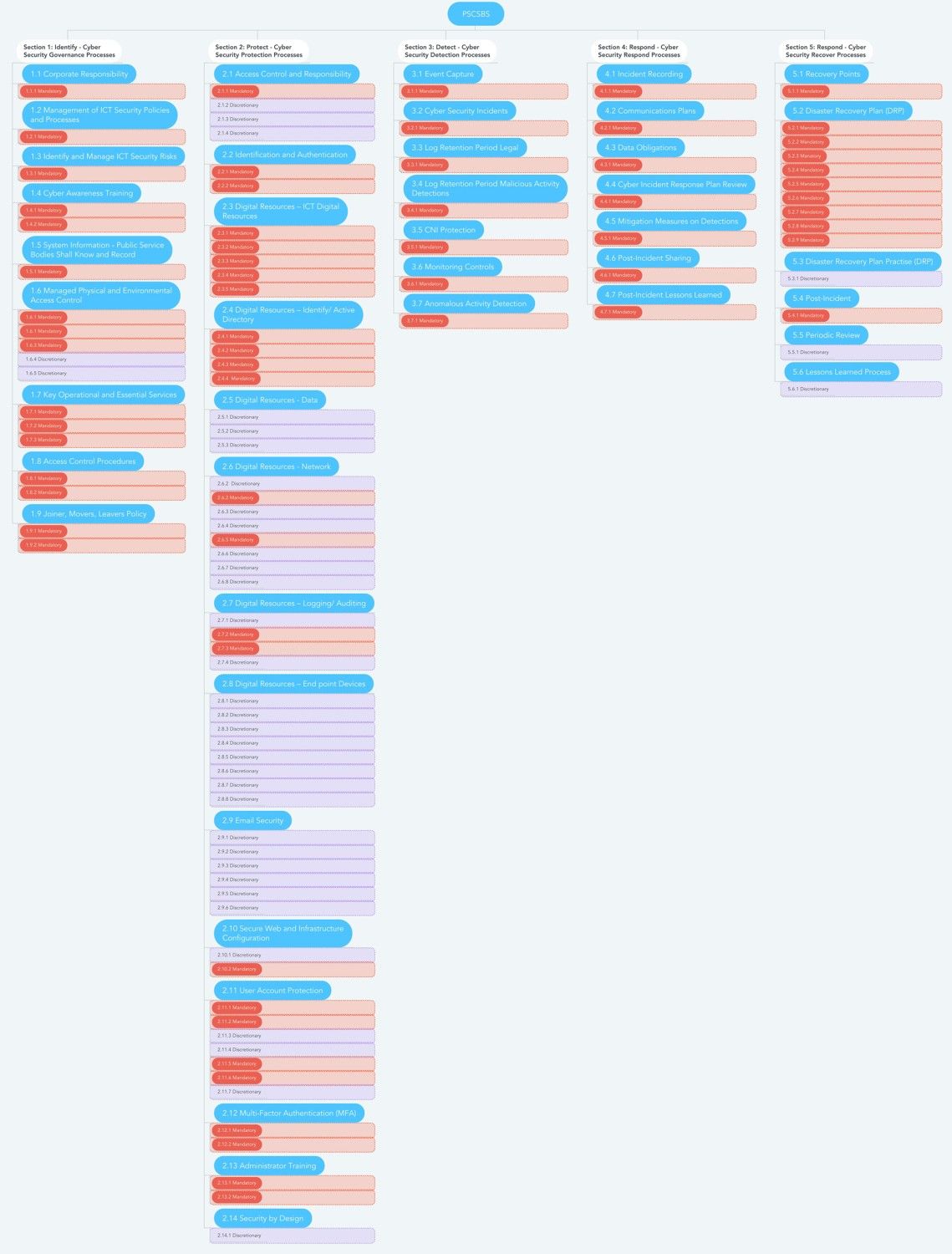
Copyright Paul C Dwyer - Full High Res Version Available Upon Request
Empty space, drag to resize
What is the goal of the IDENTIFY function?
The identify function helps organisations develop an understanding of how to manage cyber security risks to systems, people, assets, data, and capabilities. It involves identifying physical and software assets within the organisation to establish an asset management program, understanding the business environment and the organisation's role in the supply chain, identifying cyber security policies and legal and regulatory requirements, and identifying asset vulnerabilities and threats to internal and external organisational resources. It also involves establishing a risk management strategy and supply chain risk management strategy, including risk tolerances and assumptions used to support risk decisions related to managing supply chain risks. The goal of the identify function is to enable organisations to focus and prioritise their efforts to manage cyber security risks in a way that is consistent with their risk management strategy and business needs.
What is the goal of the PROTECT function?
The protect function outlines the appropriate safeguards to ensure the delivery of critical infrastructure services and supports the ability to limit or contain the impact of a potential cyber security event. It covers protections for identity management and access control within the organization, including physical and remote access, as well as empowering staff through awareness and training, including role-based and privileged user training. It also includes establishing data security protections that are consistent with the organisation's risk strategy to protect the confidentiality, integrity, and availability of information, implementing information protection processes and procedures to maintain and manage the protections of information systems and assets, and protecting organisational resources through maintenance activities. Additionally, the protect function involves managing protective technology to ensure the security and resilience of systems and assets are consistent with organisational policies, procedures, and agreements.
What is the goal of the DETECT function?
The detect function defines the appropriate activities to identify the occurrence of a cyber security event and enables timely discovery of such events. It involves ensuring that anomalies and events are detected and their potential impact is understood, implementing security continuous monitoring capabilities to monitor cyber security events and verify the effectiveness of protective measures, and maintaining detection processes to provide awareness of anomalous events. The goal of the detect function is to enable organisations to quickly identify cyber security events and take appropriate action to mitigate their impact.
What is the goal of the RESPOND function?
The respond function includes appropriate activities to act in response to a detected cyber security incident and supports the ability to contain the impact of a potential cyber security incident. It involves executing response planning processes during and after an incident, managing communications with stakeholders, law enforcement, and external stakeholders as appropriate, conducting analysis to ensure effective response and support recovery activities, including forensic analysis and determining the impact of incidents, and performing mitigation activities to prevent the expansion of an event and to resolve the incident. The organisation also implements improvements by incorporating lessons learned from current and previous detection and response activities. The goal of the respond function is to enable organisations to effectively respond to cyber security incidents and contain their impact.
What is the goal of the RECOVER function?
The recover function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cyber security incident. It supports timely recovery to normal operations to reduce the impact of a cyber security incident. This function involves implementing recovery planning processes and procedures to restore systems and/or assets affected by cyber security incidents, implementing improvements based on lessons learned and reviews of existing strategies, and coordinating internal and external communications during and following the recovery from a cyber security incident. The goal of the recover function is to enable organisations to quickly recover from cyber security incidents and return to normal operations.
How do I comply?
Visit www.cri.ie and join the webinar on January 10th at 11:00. CRI will outline your FastTrack route to compliance.
The identify function helps organisations develop an understanding of how to manage cyber security risks to systems, people, assets, data, and capabilities. It involves identifying physical and software assets within the organisation to establish an asset management program, understanding the business environment and the organisation's role in the supply chain, identifying cyber security policies and legal and regulatory requirements, and identifying asset vulnerabilities and threats to internal and external organisational resources. It also involves establishing a risk management strategy and supply chain risk management strategy, including risk tolerances and assumptions used to support risk decisions related to managing supply chain risks. The goal of the identify function is to enable organisations to focus and prioritise their efforts to manage cyber security risks in a way that is consistent with their risk management strategy and business needs.
What is the goal of the PROTECT function?
The protect function outlines the appropriate safeguards to ensure the delivery of critical infrastructure services and supports the ability to limit or contain the impact of a potential cyber security event. It covers protections for identity management and access control within the organization, including physical and remote access, as well as empowering staff through awareness and training, including role-based and privileged user training. It also includes establishing data security protections that are consistent with the organisation's risk strategy to protect the confidentiality, integrity, and availability of information, implementing information protection processes and procedures to maintain and manage the protections of information systems and assets, and protecting organisational resources through maintenance activities. Additionally, the protect function involves managing protective technology to ensure the security and resilience of systems and assets are consistent with organisational policies, procedures, and agreements.
What is the goal of the DETECT function?
The detect function defines the appropriate activities to identify the occurrence of a cyber security event and enables timely discovery of such events. It involves ensuring that anomalies and events are detected and their potential impact is understood, implementing security continuous monitoring capabilities to monitor cyber security events and verify the effectiveness of protective measures, and maintaining detection processes to provide awareness of anomalous events. The goal of the detect function is to enable organisations to quickly identify cyber security events and take appropriate action to mitigate their impact.
What is the goal of the RESPOND function?
The respond function includes appropriate activities to act in response to a detected cyber security incident and supports the ability to contain the impact of a potential cyber security incident. It involves executing response planning processes during and after an incident, managing communications with stakeholders, law enforcement, and external stakeholders as appropriate, conducting analysis to ensure effective response and support recovery activities, including forensic analysis and determining the impact of incidents, and performing mitigation activities to prevent the expansion of an event and to resolve the incident. The organisation also implements improvements by incorporating lessons learned from current and previous detection and response activities. The goal of the respond function is to enable organisations to effectively respond to cyber security incidents and contain their impact.
What is the goal of the RECOVER function?
The recover function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cyber security incident. It supports timely recovery to normal operations to reduce the impact of a cyber security incident. This function involves implementing recovery planning processes and procedures to restore systems and/or assets affected by cyber security incidents, implementing improvements based on lessons learned and reviews of existing strategies, and coordinating internal and external communications during and following the recovery from a cyber security incident. The goal of the recover function is to enable organisations to quickly recover from cyber security incidents and return to normal operations.
How do I comply?
Visit www.cri.ie and join the webinar on January 10th at 11:00. CRI will outline your FastTrack route to compliance.
Empty space, drag to resize
Paul C Dwyer is the CEO for Cyber Risk International
recognised as one of the world’s foremost experts on cyber security, risk and privacy. Connect to Paul here.
recognised as one of the world’s foremost experts on cyber security, risk and privacy. Connect to Paul here.


HEAD OFFICE
-
ICTTF Ltd
ICTTF House
First Floor Unit 15
N17 Business Park
Tuam, Co Galway
H54 H1K2 -
info@icttf.org
support@icttf.org -
+353 (0)1 905 3263
Copyright © - All Rights Reserved - ICTTF Ltd. - Registered Company in Ireland: 567446 - VAT No IE3395678DH

