
What is an E-Skimming Attack?
What is an E-Skimming Attack?
An e-skimming attack (aka ‘Magecart Attacks’, a name associated with a threat group that uses digital skimming techniques to steal customer data) is a very attractive method of attack for hackers because it doesn’t require them to deploy malware or compromise a system. Instead, they identify a weakness in a system and exploit it by injecting malicious JavaScript code into the target website’s e-commerce platform. This enables them to take control of the information capturing sections of a website, such as the “checkout” process, to collect sensitive user information.
How Does an E-Skimming Attack Work?
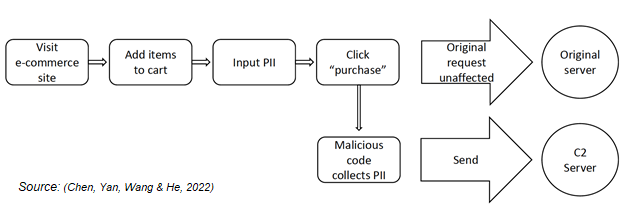
An internet surfer accesses an e-commerce website to browse and decides to purchase a particular item. They add the product to their shopping cart and proceed to purchase it. They are directed to enter their personal details (personally identifiable information, ‘PII’) to complete the purchase. These details may include their name, delivery address, email address, phone number, credit card number, expiry date, CVV etc.). They click “purchase”, exit the site and wait for their delivery. The individual will have no knowledge that their data has been stolen unless or until it is used in an unauthorised online purchase by the hacker. The original purchase is not affected by this malicious activity and the consumer receives their purchase.
On the dark side of this purchasing activity, when the customer enters their CVV code and clicks “purchase”, the malicious code is triggered and launches, collecting the submitted PII and sending it to the threat actor’s Command & Control server (C2) for storage and later use. It then goes dormant and waits for the next customer to do the same. The collected personal data may be sold on the dark web or used by the criminal to make fraudulent purchases.
Attack Process Flow
An e-skimming attack (aka ‘Magecart Attacks’, a name associated with a threat group that uses digital skimming techniques to steal customer data) is a very attractive method of attack for hackers because it doesn’t require them to deploy malware or compromise a system. Instead, they identify a weakness in a system and exploit it by injecting malicious JavaScript code into the target website’s e-commerce platform. This enables them to take control of the information capturing sections of a website, such as the “checkout” process, to collect sensitive user information.
How Does an E-Skimming Attack Work?
An internet surfer accesses an e-commerce website to browse and decides to purchase a particular item. They add the product to their shopping cart and proceed to purchase it. They are directed to enter their personal details (personally identifiable information, ‘PII’) to complete the purchase. These details may include their name, delivery address, email address, phone number, credit card number, expiry date, CVV etc.). They click “purchase”, exit the site and wait for their delivery. The individual will have no knowledge that their data has been stolen unless or until it is used in an unauthorised online purchase by the hacker. The original purchase is not affected by this malicious activity and the consumer receives their purchase.
On the dark side of this purchasing activity, when the customer enters their CVV code and clicks “purchase”, the malicious code is triggered and launches, collecting the submitted PII and sending it to the threat actor’s Command & Control server (C2) for storage and later use. It then goes dormant and waits for the next customer to do the same. The collected personal data may be sold on the dark web or used by the criminal to make fraudulent purchases.
Attack Process Flow
How can an Organisation Prevent E-Skimming?
E-commerce websites are built with hundreds of thousands and often millions of lines of code, making it very easy for cyber criminals to hide the malicious code needed for this attack. E-commerce sites are heavily built using JavaScript which is not inherently secure, making it easy to infiltrate.
Assume you are vulnerable. It is advised that retailers using e-commerce platforms practice comprehensive patch management. It is best practice to regularly conduct web content integrity checks offline to assess if your pages were edited or hold malicious code which would have been inserted by attackers. Ensure there are strong passwords on your content management system (CMS) to make it less susceptible for brute force attacks. Website administrators should monitor and manage user permissions to remain in control of access rights. If you are using 3rd party services for web page analytics, plug-ins etc., be cautious that this increases the attack surface for hackers and you should regularly analyse the cyber maturity of those services.
Employee training is crucial for reducing overall risk to your company. Unfortunately, people are often the weakest link in the attack surface for hackers. Create a culture of care towards cyber security and train your employees to be proactive and question things, providing them with a trusting environment to do so. Employees need to be vigilant, well-informed and should enhance your front-line defenses.
Sources: Chen, J., Yan, T., Wang, T., & He, Z. (2022). Anatomy of Formjacking Attacks Anatomy of Formjacking Attacks. Retrieved 27 January 2022, from https://unit42.paloaltonetworks.com/anatomy-of-formjacking-attacks/ What is E-skimming?. (2022). Retrieved 27 January 2022, from https://www.feroot.com/education-center/what-is-e-skimming/
Stone, J., & Willis, A. (2022). How to Prevent Formjacking and E-commerce Skimming (Magecart Attacks). Retrieved 27 January 2022, from https://www.securitymetrics.com/blog/how-to-prevent-formjacking-ecommerce-skimming-magecart
Ella O’Neill is a Cyber Agent at ICTTF
E-commerce websites are built with hundreds of thousands and often millions of lines of code, making it very easy for cyber criminals to hide the malicious code needed for this attack. E-commerce sites are heavily built using JavaScript which is not inherently secure, making it easy to infiltrate.
Assume you are vulnerable. It is advised that retailers using e-commerce platforms practice comprehensive patch management. It is best practice to regularly conduct web content integrity checks offline to assess if your pages were edited or hold malicious code which would have been inserted by attackers. Ensure there are strong passwords on your content management system (CMS) to make it less susceptible for brute force attacks. Website administrators should monitor and manage user permissions to remain in control of access rights. If you are using 3rd party services for web page analytics, plug-ins etc., be cautious that this increases the attack surface for hackers and you should regularly analyse the cyber maturity of those services.
Employee training is crucial for reducing overall risk to your company. Unfortunately, people are often the weakest link in the attack surface for hackers. Create a culture of care towards cyber security and train your employees to be proactive and question things, providing them with a trusting environment to do so. Employees need to be vigilant, well-informed and should enhance your front-line defenses.
Sources: Chen, J., Yan, T., Wang, T., & He, Z. (2022). Anatomy of Formjacking Attacks Anatomy of Formjacking Attacks. Retrieved 27 January 2022, from https://unit42.paloaltonetworks.com/anatomy-of-formjacking-attacks/ What is E-skimming?. (2022). Retrieved 27 January 2022, from https://www.feroot.com/education-center/what-is-e-skimming/
Stone, J., & Willis, A. (2022). How to Prevent Formjacking and E-commerce Skimming (Magecart Attacks). Retrieved 27 January 2022, from https://www.securitymetrics.com/blog/how-to-prevent-formjacking-ecommerce-skimming-magecart
Ella O’Neill is a Cyber Agent at ICTTF

HEAD OFFICE
-
ICTTF Ltd
Unit 8, Kinsealy Business Park,
Kinsealy Lane,
Malahide,
Co Dublin
K36 CX92 -
info@icttf.org
support@icttf.org -
+353 (0)1 905 3263
Copyright © - All Rights Reserved - ICTTF Ltd. - Registered Company in Ireland: 567446 - VAT No IE3395678DH
