
Zero Trust and Trusted Partners:
Elements of Israel’s approach to
cyber security
GUEST BLOG
According to CheckPoint Research (CPR), a leading provider of cyber threat intelligence, Q2 of
2022 saw an all-time peak in global cyber-attacks; an increase of 32%, compared with the same
period in the previous year. This increase should be a further call to action; not only of industry and
governments, but to all those who operate in the digital landscape, that they must enhance their
collaboration in combating cyber threats.
Such developments are taking place in Israel, where earlier this year the Israel National Cyber Directorate (INCD) and Israeli Ministry of Communications announced new regulations and mandatory cybersecurity standards to combat the rise in digital attacks. Israeli communications services are now required to implement various measures to bolster their digital defenses, such as conducting frequent vulnerability scans and applying protection standards for suppliers and contractors.
Such developments are taking place in Israel, where earlier this year the Israel National Cyber Directorate (INCD) and Israeli Ministry of Communications announced new regulations and mandatory cybersecurity standards to combat the rise in digital attacks. Israeli communications services are now required to implement various measures to bolster their digital defenses, such as conducting frequent vulnerability scans and applying protection standards for suppliers and contractors.
Empty space, drag to resize
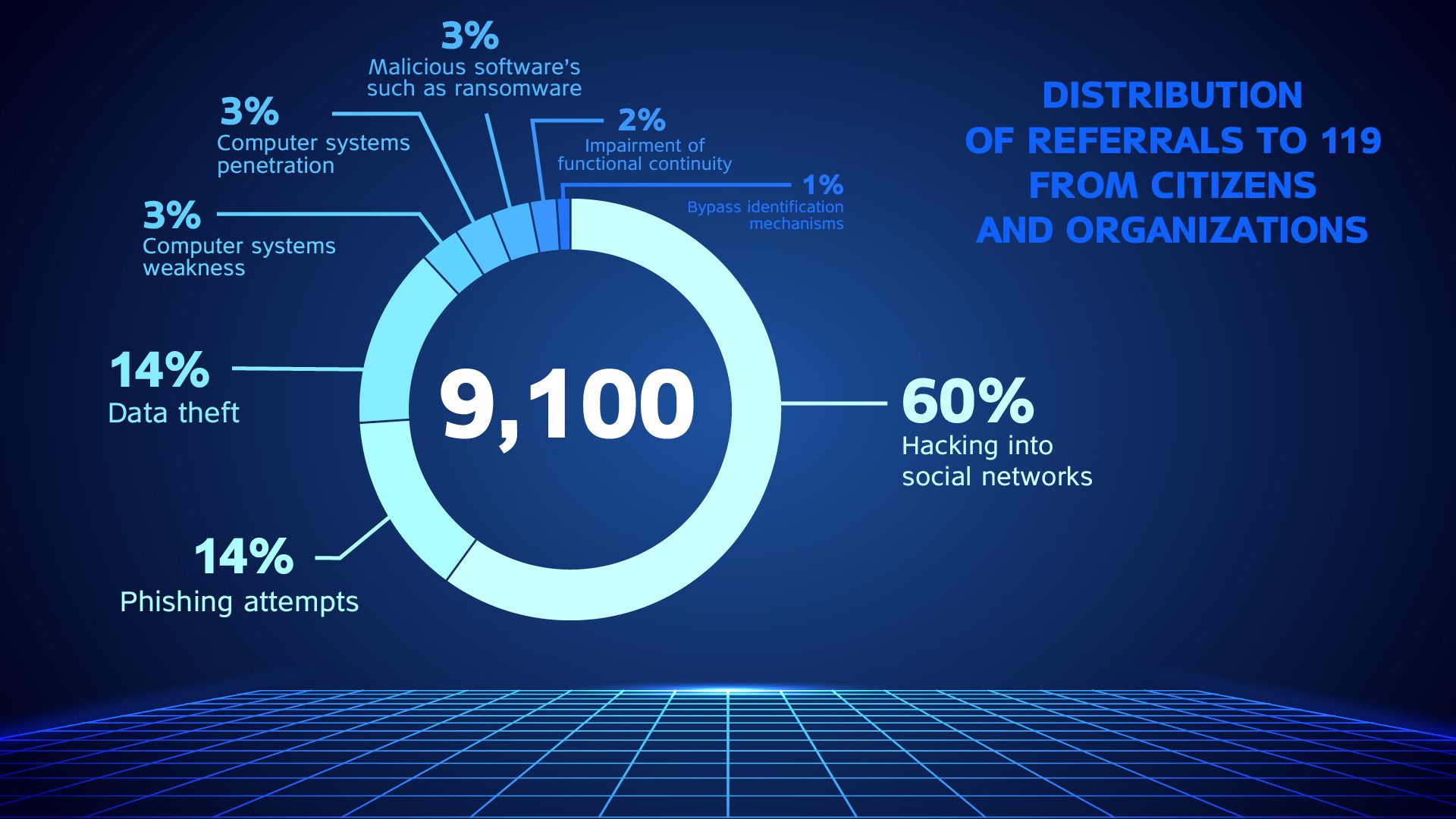
An increase of about 50% in reports to the 119 center of INCD on cyber incidents in 2020
Director General of the INCD, Gaby Portnoy recently stressed the importance of more proactive and
innovative solutions to cybersecurity. Rather than merely mitigating attacks as they arise, Portnoy
called for the establishment of a “Cyber-Dome”, a comprehensive cyber defence strategy employing
newer mechanisms for detection, analysis, and mitigation of threats. A key element of this
multifaceted cybersecurity strategy is a zero-trust approach to IT, which assumes that no user or
device can be trusted until adequately verified.
Utilizing two-factor authentication, access controls, and other elements, zero-trust is among the most effective methods of protecting against cyberattacks. Recognizing networks’ vulnerability once they have been breached, the zero-trust model implements security checkpoints at various stages to identify and isolate breaches as they occur.
While investing time and effort into improving cyber defenses places a significant burden on organisations of almost every type, Portnoy was quick to highlight the potential opportunities for companies to develop “cyber secure-by-design” products and solutions which can promote the evolution and development of; not only the indigenous cyber sector, but also of other sectors such as utilities, healthcare, transport, agriculture and finance.
Coupled with this, a high level of international cooperation and information sharing between cyber security authorities globally, public-private partnerships and multinational corporations, can significantly enhance the digital security of the global digital community.
Utilizing two-factor authentication, access controls, and other elements, zero-trust is among the most effective methods of protecting against cyberattacks. Recognizing networks’ vulnerability once they have been breached, the zero-trust model implements security checkpoints at various stages to identify and isolate breaches as they occur.
While investing time and effort into improving cyber defenses places a significant burden on organisations of almost every type, Portnoy was quick to highlight the potential opportunities for companies to develop “cyber secure-by-design” products and solutions which can promote the evolution and development of; not only the indigenous cyber sector, but also of other sectors such as utilities, healthcare, transport, agriculture and finance.
Coupled with this, a high level of international cooperation and information sharing between cyber security authorities globally, public-private partnerships and multinational corporations, can significantly enhance the digital security of the global digital community.

For more information about Israel’s Cyber Security Industry please visit:
1) Israel National Cyber Directorate - https://www.gov.il/en/departments/israel_national_cyber_directorate/govil-landing-page
2) Israel Export Institute Cyber Sector - https://www.export.gov.il/en/cyber
1) Israel National Cyber Directorate - https://www.gov.il/en/departments/israel_national_cyber_directorate/govil-landing-page
2) Israel Export Institute Cyber Sector - https://www.export.gov.il/en/cyber
Colin Sheena is the Commercial Representative at the Embassy of Israel in Dublin. The Commercial
Office works to generate, promote and enhance bilateral trade, investment and economic
cooperation with Ireland.
Connect to Colin here.
Connect to Colin here.

HEAD OFFICE
-
ICTTF Ltd
Unit 8, Kinsealy Business Park,
Kinsealy Lane,
Malahide,
Co Dublin
K36 CX92 -
info@icttf.org
support@icttf.org -
+353 (0)1 905 3263
Copyright © - All Rights Reserved - ICTTF Ltd. - Registered Company in Ireland: 567446 - VAT No IE3395678DH
